Yesterday's news about two Federal Agents arrested for various allegedly corrupt and self serving actions has introduced a substantial number of complications that could jeopardize the government's case on appeal. The charging document (plain text document image) rather than merely affecting the future disposition of the Ulbricht Silk Road case offers a number of lessons on operational security people involved with can take to heart as well as a good number of laughs.
First, the United States Government is extremely capable of tracking its dollars, and its institutions are adept at noticing and investigating "inexplicable" sums of dollars that find their way into people's hands. Simply if your fiat holdings in the bank don't fit the profile of what the Government knows about you, you are going to get attention. If you raise a fuss with any institution that handles United States dollars like BitStamp or any PayPal subsidiary they are in all likelyhood going to start filing suspicious activity reports with their regulators. Especially if like Force is alleged to have done you go so far as to request they delete all your history or fake a subpoena in order to have an account unblocked.
Second, your signature should be hard for an attacker to fake. A signature stamp, of the sort Force's boss had and Force was alleged to have used to fake the subpoena is not a thing that should exist. For the slightest bit of extra convenience you add to yourself in the process of signing, you can gain for yourself a much stronger signature. Gnu Privacy Guard is good, and airgapped and physically secured machine for creating signatures is better.
Third, if you aren't running what everyone else is running taking small steps to obscure that fact can go a long way. Consider this bit of circumstantial evidence which the government alleges connects Force to one of his extortion sockpuppets:
Additional pieces of circumstantial evidence prove that FORCE is "French Maid." Both "French Maid" and FORCE (operating as "Nob") used the exact same brand of PGP software, a free brand called GnuPG. There are different brands of PGP software so it is noteworthy that both FORCE (operating as "Nob") and "French Maid" used the same brand. Not only did FORCE and "French Maid" both use the same brand of PGP software, they also both used the same outdated version of that software, 1.4.12. Version 1.4.12 was released on January 2012, and was replaced with a new version by December 2012, and was one of several versions of GnuPG software,[14] As such, both "French Maid" and FORCE (as Nob) were using a specific, older version of the GnuPG software, and neither of them replaced it with the other (free) versions of GnuPG that came out thereafter.
I know based on conversations with another federal agent who is involved in undercover investigations that among TOR users and consumers or PGP software, v1.4.12 version was somewhat outdated by late August 2013 when “French Maid" appeared in communication with DPR for the first time. This is not akin, for example, to two people using the same model of mobile phone but both having software that is out of date. Rather, the outdated version that both "French Maid" and FORCE (as Nob) used is more of a "signature" given the greater number of versions available.
Now, this piece of circumstantial evidence offers no positive warrant at all that "French Maid" was Force. Most people who use GPG stay on the 1.4.x "classic" branch, and 1.4.12 is a popular version of the software many people stop upgrading at because they worry about various turds being inserted by malefactors in newer versions. Still as worthless as this circumstantial evidence is you can make your version strings omit part of the version number, omit the entire version number, or simply outright lie.
Fourth, plan for a Nation-State adversary. It is harder than simply trying to stay a few steps a head of script kiddies, assuming you have nothing that demands security, or simply hoping for the best. Preparing your security model against a Nation-State adversary however offers protection against the lesser threats in life who might choose an adversarial relationship against you. It offers insulation against the script kiddie, the nosy neighbor, the private investigator, and the jilted former lover. Maybe you don't ever get to the point of completely resisting a focused nation state attacker, but being a harder target than the other schmucks increases the cost to an adversary and might permit being the member of the group who outruns the bear. The full spectrum of things deemed illegal is a known unknown and for that reason any number of your secrets could require the most serious protection. The Nation-State adversary as threat model is especially true if your profession is law enforcement.
Fifth, conduct yourself as though a day of reckoning is an eventual certainty. Force had a habit of throwing his profession around in a way that if Bitcoin villain Mark Karpeles can be believed leads to exchanges like this:
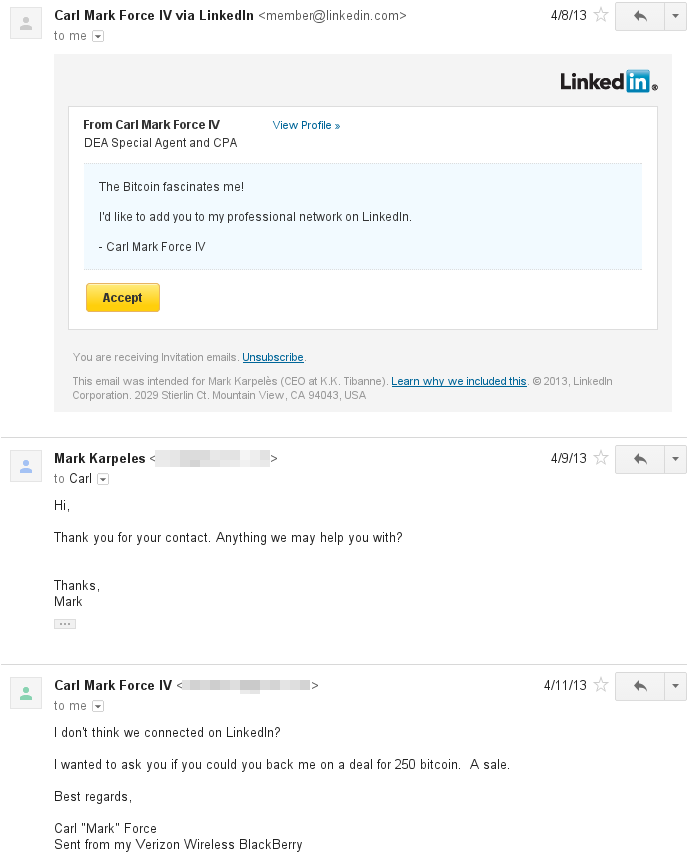
The last thing anyone ought to want to be seen as is the nerdier Federal Version of Denzel Washington from Training Day.
Sixth, for the Nation-State adversaries though they likely know this already, Bitcoin will outlast you. In this instance you managed to catch two agents who had sworn loyalty to you and turned to their own benefit, however you only managed to succeed in this instance because of their industrious stupidity and brazen actions. The next crop to make these decisions will likely be harder to catch. What if the Bitcoin Force managed to extort from the Dread Pirate Roberts was not converted to cash and alternate universe Force kept the Bitcoin as such and quietly moved it, mixed it, and tumbled it over the several years or decades? What if instead of an Aldrich Ames who spent extravagantly from his gains, you faced a Robert Hansen who never spent ostentatiously yet once his treachery began never felt urgent financial desperation.
I seem to recall that Force was unwise enough to use his office computer for some of his illicit activities. The reason they knew about some of his activities, is that security software periodically takes screenshots of user activitity, and backs these up to a central server.
If he had used a second-hand laptop, Tails, and some obscure coffee-shop's WiFi, he may very well have gotten away with it.
This is a point.
Robert Hansen -> Robert Hanssen
The former is a serial killer.
And neither one is a Nigerian prince.